We often mention that complete privacy and the Internet do not meet despite all the companies' attempts to close the holes in their systems and make it safer, but we always find security holes, and we mentioned the UDID and how it was It represents a privacy security vulnerability Apple prompted to warn developers against using it. But there are many other loopholes that hackers seek to discover day and night, which represent a huge profit for them. Recently, the US Congress has put pressure on companies to increase user privacy, and indeed companies are doing so Gradually increasing the degree of safety But did you know that there is a vulnerability in your device that could lead to knowing your phone number and name despite all the precautions you take? Read with us this advice that is unique to iPhone Islam to present it for the first time ...
Any application that can access your list of names but can never know your name or phone number or any information about you and this is good of course because your identity remains unknown to everyone, but the danger is that the application can know the name of your device, if the name of your device is identical to your name in the caller list In your phone, the application may be able to record this information and it is almost sure that this information is the information of the owner of the device because most users register their personal numbers on their phones with their personal name or nickname that they use.
Steps that the app uses to find out your personal information:
- Get all phone numbers.
- Know the name of the device.
- Searching in the list of names and accessing the phone number registered under the name of the owner of this device and thus knows your number and all other information.
- Repeat this command on hundreds of thousands of connected devices, knowing their names.
- Linking phone numbers to each other in the event of repetition and perhaps knowing family ties if you registered the number (my uncle - my uncle) and this uncle uses the same application and records his name.
- Now the developer has a huge file that includes people's names, phone numbers, types, and locations (if the application specifies the location), family links and other information, meaning that he has a huge commodity for sale and a serious security hole.

All of the above is a hypothetical expectation to abuse an existing vulnerability (and there is nothing to confirm that it is actually happening for the purpose of espionage), but it may happen or perhaps the security services do this, so it is preferable that the name of your device is different from the name with which you register your phone number in the contacts list.
So review the name of your device now and others for something that does not refer to you, and you can change the name of your device in two ways:
1
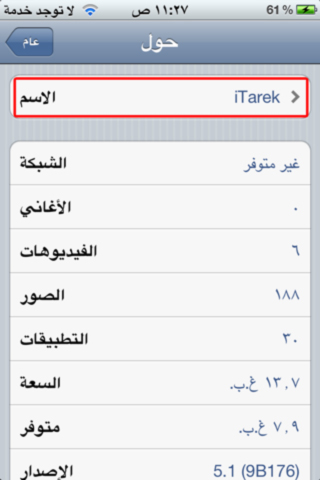
From the phone itself (only on iOS 5): Settings> General> Information> About, so you can find the name and change it.
2
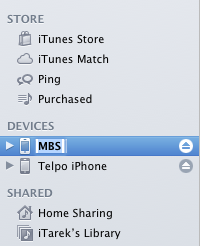
From the iTunes program, click on the name of the phone, and the possibility of modification appears.



182 comment