devices Camel It is considered the safest compared to the devices of other competing companies, as it continuously enhances protection in order to ensure the security of user data and prevent any attempt to access it, but this does not mean that its devices are completely immune, as security researchers found a vulnerability in the iPhone, iPad and Mac devices, which can be exploited It may allow hackers to access important files and information of the victim.

A loophole in the iPhone, iPad and Mac

Apple corrected and fixed serious security vulnerabilities found by Trellix by launching the macOS 13.2 and iOS 16.3 updates, and Apple did not stop at this point, but introduced another new version of the operating system for Mac and iPhone and most of its devices, which included security fixes for some vulnerabilities that were exploited on devices other users.
To avoid all this, you just have to make sure that you update your operating system when a new version is available, it is not a luxury or an option, update your device before you become a victim of a hack
The seriousness of these vulnerabilities, and why they should update your device
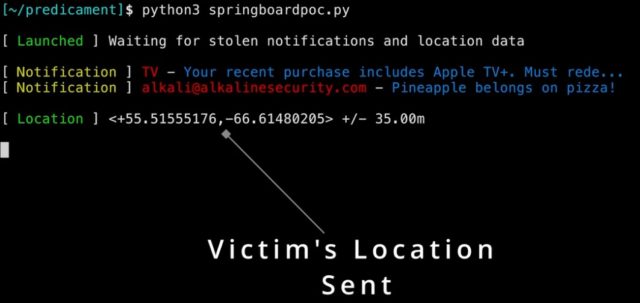
Researchers affiliated with the cybersecurity company Trellix published details of a vulnerability that could allow hackers to bypass protection measures provided by the company in the iPhone and Mac operating system and then run unauthorized code. Although the vulnerability was classified as medium to high risk, it could It gives hackers access to sensitive data, including messages, photos, even your call history, notifications, and your current location.
Trellix researchers' findings are based on a vulnerability ForcedEntry Which was discovered by Google in cooperation with the Citizen Lab security organization based at the University of Toronto in 2021 and that vulnerability is called the zero click and was used by the Zionist entity company NSO Group to penetrate the iPhone and then install its malicious program, Pegasus, without the need for the victim to interact and even without him knowing.
And the analysis of the ForcedEntry vulnerability showed that the hackers relied on two things, the first was to deceive the iPhone to open a malicious PDF file disguised as a moving image. The second part allowed hackers to bypass the protection mode imposed by Apple on the iPhone operating system, which prevents applications from accessing data stored by other applications and also restricts access to other places on the device.
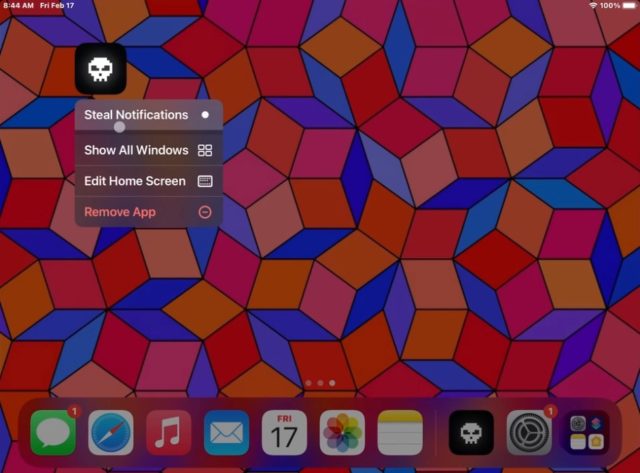
Ost Emmett, a researcher at Trellix, focused on the second part, which revolves around how to bypass the protection mode on the iPhone, where Emmett found some vulnerabilities that revolve around nspredicate (a tool for filtering code inside the operating system), which was exploited for the first time by the ForcedEntry vulnerability, except that Apple fixed the matter in 2021, but it seems that this was not enough, as the researchers of the cybersecurity company were able to find new vulnerabilities that could be exploited and bypass the sandbox. in Apple devices.
The researchers said the new bugs in the NSPredicate tool are present in multiple places on macOS and iOS, including within Springboard, the app that manages the iPhone's home screen, controls the user interface, and can access location data, photos, and the camera. Once this vulnerability is exploited, the hacker can gain access to unauthorized places. But according to the researchers, a hacker has to gain a foothold in the victim's machine, which means they have to find a way in before exploiting the vulnerability in the NSPredicate tool.
Source:



11 comment