There is no doubt that the issues of privacy and confidentiality in your use of the iPhone are of utmost importance in the smartphone community, its users, developers and even its companies, so we talk a lot about it to educate everyone about the importance of this matter, especially with the large spread of smartphones around the world and its recent popularity and what this popularity will inevitably cause from the spread of penetration Privacy, confidentiality and user information theft.
We reviewed Previously, ways to protect the iPhone and your data on it, including the Find My iPhone service of Apple's paid me.com service, which accurately locates the stolen iPhone and enables you to control it remotely, such as closing it and wiping its data, but Apple seems to think that this is not enough to come to us. With a patent registered in its name recently and very advanced, its job is to catch the thief of your device and record its data with great accuracy! Yes, do not be surprised when you read the mechanism of action of this invention as it does the following:
- Voice recording from the hand of the iPhone currently.
- Take his photo.
- Determine its location geographically.
- Moreover, running the accelerometer or the Accelerometer to determine the position and movement of the device currently in the hands of the user and thus determine the position of its holder!
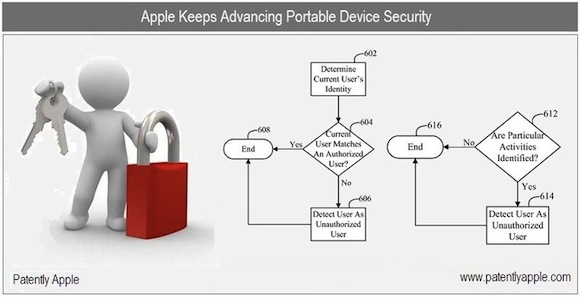
This invention takes multiple random pictures from the iPhone remotely without any "flash" so that no one feels that these pictures are taken and sends them to Apple for analysis and trying to find out the location and position of the user. This technology then notifies the user Binder By Apple (i.e. the original owner of the iPhone) through multiple means such as SMS or instant messages or VoIP calls that someone uses his device, then it then transfers sensitive data to a remote provider for safekeeping and then wipes all the data on the phone Present. Also, this technology disables some capabilities and features of the device to become unusable.
What is more, this technology may use highly sophisticated methods to determine the reliability of the current user of the device or not, such as a special sensor to determine the heartbeat of the current iPhone user to verify it, as well as some well-known methods such as determining the number of times to enter the correct password before shutting down the phone!

To here, this technology may seem very sophisticated and imaginative, especially the part about identifying the heartbeat and tension of the user, and at the same time it raises horror, we know that many major companies such as Google, Microsoft, Facebook and others have a lot of real sensitive information about their users and any wrong or harmful use in this The information may expose these companies to loss of credibility and consequently the loss and loss of their users, and we have seen how the taking of a few pictures by Google on the streets in European and Asian cities sparked a sensation against them and legal claims in the courts, which led to their retreat, recognition and apology. Therefore, any misuse of this information is a suicide for these companies, especially with the fierce competition.
But the problem with Apple is not here, but in its definition of Trusted User It considers, for example, that whoever uses jailbreaking, unlocking the protection and unlocking the network, or using unauthorized or pirated programs, is an untrusted user who may lead to the application of that technology on him and thus expose his information and breach his privacy, and this is what many bodies raised after the news of this new invention was published. Camel.
It is good for Apple to seek to keep the user’s devices from being stolen in these advanced ways, but what about the "legality" of the jailbreak as recognized by some US courts, what about the privacy of its users, and what about the wrong and dangerous use of this technology in other forms?
We think Apple has a lot to explain on this topic. We believe that not every patent is suitable for actual execution. What do you think?

Was this invention implemented ???
Brothers please help
The iPhone was stolen while I was outside the country, and when I came back, I called the calls on the basis that they disrupted it and said that it was disabled, and I honestly am not sure whether or not the Find my iPhone program has something very special
Is there a way that I can be sure that the device has really broken down, and can you wipe all the things in it?
The second question, is it possible for him to come back to me or forget?
I live in Italy and my iPhone XNUMXGS was stolen and I reached Apple, but they apologized for finding it as long as I am not subscribed to Mi Mobile, and they asked me to notify the police and frankly, I was surprised and if the article was correct and I hope so, why did they not want any help? The theft was XNUMX days ago? !!! ...
And God is very strange
Actually once serious God conceals
My mobile guys are regular and who bought the company, but I miss the system. Is there a risk to me and a campaign, and then who will determine the site? I or the company?
Serious God
But it would really be a problem for those who use the jailbreak
It can also be a service that we can control (cancel, activate)
Simple to keep a sticker on the camera like what some people do on laptops
The idea is dangerous and it must be applied accurately
It means it is optional for the user
It is activated after his request if he lost his device
Because he is lesser than them presumably, and this will become a lot. I gave my eve to my niece or sister or anyone
Will this property be applied to it?
Exposing such-and-such
Likewise, if it is applied to jailbreak users
God Almighty the whole world rested in it
Most of the people I know are gerblick users (despite my reservations)
Go back and say the idea is excellent with proper application
Certainly, we shall not judge until after we hear the opinion of the company and its preference for the subject
All thanks to Yvonne Islam
Great patent, but will it be applied?
Devices are dear to us, dear to our hearts, and worth a return
Espionage is present on your regular mobile phone if you do not know from messages to calls to BlackBerry users and even Internet users
Let espionage benefit us, even once
By God, Apple is a very strong company
No privacy with technology and government story
In fact, this is a pioneering and effective step, and I hope the national team wins and solves the bluetooth problem
in my opinion
This is Apple's response to the Jailbreak after they won
The case is in the American courts
I think that since the nineties of the last century and the developments that it carried, there is no longer any room to talk about something called privacy, or rather, the concept of privacy and its limits must be reconsidered. And whoever wants to preserve his privacy in the old concept is delusional or what he has to do is distance himself from society and The history is in an underground cave where there are no surveillance cameras, no net, no GPS signal or satellite detection.
Now, basically, there is no privacy if you are on the internet or talking on the mobile phone or any private information of yours. Believe it or not, our governments know everything about the Arabic net user.
My personal opinion is that Apple is more merciful than our oppressive governments, even if they spy on iPhone owners, they will not take them and see the sun, or an underground prison.
Which sun and any land .. This is just a lie that has become in circulation at one time and unfortunately there are still people who believe it and promote it
We, praise be to God, live in peace and security
To be honest, a respectable company. And she deserves all respect
Every year and everybody's okay
Espionage is going on from the beginning ... This is an opinion
It will be an espionage tool, of course.
I expect if Apple focuses on filling the iPhone's gaps, it will be better for it.
And I don't expect every patent to be executed.
Frankly, I don’t doubt that Apple can access our devices now, and it is the current situation, because the iPhone XNUMX hours is connected to the Internet, and we don’t know if there is a loophole that Apple left in one of its iPhone programs to use for its own purposes.
First of all, this invention is considered the greatest evidence of Apple's keenness and constant pursuit of perfection (perfection is God) and its keenness on the comfort and happiness of their customers. I believe that it is still too early to judge the feasibility of this invention, as everything is subject to experience, and then we will see what is the reality after that. As for the issue of espionage, I say to my dear brothers who are afraid of it that modern technology is originally the property of a toxic uncle (: This is how the cycle of civilization decided - without delving into the causes and causes - that they are the ones concerned with technology. Who knows, perhaps espionage has existed from the beginning, can he Can anyone deny that? God knows
Long as you
There is a Chinese phone in the market, and in the event that it is stolen and its SIM card is changed, it only calls one number, which is set by the owner of the original device, and no one can change it except the owner of the original device. That is, the thief will not benefit from anything from the device because he will only call one phone number ... hahahahahahahaha
This is what we have been watching in science fiction movies. Wonderful and amazing. I hope to see Islamic minds succeed as Apple's successes.
Wonderful and much more wonderful
Apple is right, you do this because it will do terrible things on the iPhone XNUMX, so this service is for important things. Any breach that occurs to the device by hackers will send a message to Apple's servers to recognize it, and then Apple works to withdraw a copy of the information on the device and then destroy it, and this is difficult for any Someone hacks the device
Because Apple intends to make the iPhone your own wallet, in which to put the passport, identity card, and credit cards ……….
I ask the managing editor to search for these rumors and write them for us in his wonderful manner
A very wonderful technology, even if an accomplished dish, the market for all other devices will be lost.
Hi
When I get your device
1 Airplane mode before connecting my pocket: d
2 restores
3 setup as a new iphone: d
Even if you do all this ,, you cannot change the serial number and I will be able to know your location because you will not be able to operate the Airplane Mode because I lock the device
You are a beginner thief ,,
Something scares!
However, can Apple really settle it !!
Thanks iPhone Islam, the strange news!
Worrying and very dangerous for someone to be able to photograph you with your device and take your picture !! Starting today, I will not enter the iPhone into my bedroom, but if Apple does not seriously explain the issue, I will replace the iPhone with another device.
For this degree? I do not expect that it is worth all these precautions .. If you are a targeted person, believe me. If you live in a cave, they will answer you, so live your life, uncle. For those who enter the bedroom, leave the iPhone in a second room غرف
A great idea if I will buy an iPhone and give it to my fiancée and know her heartbeat as she talks to me ... and see her without makeup and the first thing she wakes from sleep ... hahahahahahaha
Hahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahahayer and you are in a world and they are in a world
But she is not afraid of her fiancée all days, and she shows her in front of you not from the mobile
Patience is the key to relief
No, by God, this is a company that has turned into (FBI)!
Hopefully, God willing, you take over the tasks of Interpol too!
The idea is great, provided that it applies only after an official notification from the owner of the iPhone, but if it is from themselves or they follow the Jailbreak and Sidis, this is a privacy choice.
Thanks Yvonne Islam
I agree
Imposed after an official report from the owner of the stolen iPhone
The best way to get your iPhone or iPad Touch is with this high textology. I will be happy to put the Eviduence who stole my defic.
Another thing, it should be by subscription so the user knows that his skef is a trusted user
I like Apple Too Much
With this theft of apple products will be reduced a lot
God forbid …
Something nice, frankly, and I have a beautiful story that happened several days ago: One day someone stole a father and Yvon's cell phone from the car, and then the men had a tracking program, Arafat knew a room, and the secretary came to the right of the building, and then he called the police, but they said it is not the first theft
Spy spy spy
I know I'm afraid of spying exactly who's going
I mean, they will spy on the advanced space projects that we have, nor on atomic science, medicine and nuclear energy.
Nor, exactly, do I have to!
We do not have anything Arab spying
No one is spying on us except for some of the people afraid of the chairs of government. Ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha-ha
you are right
You are right, I mean, I have a reactor, and I am afraid of it all. If it goes to Moya, it will be destroyed and thrown
I meant, honestly, this statement: "I mean, they will spy on the advanced space projects that we have, nor on nuclear science, medicine and nuclear energy.
Nor, exactly, do I have to!
We do not have anything Arab spying
No one is spying on us except for some of the people, afraid of the seats of government. Hahahahahahahahahahahahahahahahahahhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh what laugh
Please focus before responding. As for the fact that if it is destroyed in Moy and destroyed and that there is no nuclear reactor, it seems clear that you either did not use the iPhone before or use it as a phone only because it is not a mobile only
I think this is the fourth iphon device that I use and I know all the uses of the device, but the one has got a lot of updates, I mean, for example, now the device that I have has become defective because I have its network in iTunes, and at the time the ironing board, the right to connect is defective, you do not see the numbers, I need to update it to 4.1.2. See what I do.
Our people expected that everyone who came and went to use it and see the peculiarities of others is naturally afraid of spying on personal matters, bank data, secret numbers, pictures ... etc.
As for the nuclear work Haha, it is for Iran and others
We are the people of God’s Gate, and we praise God for the side of the Hitt
Most of the internet users in the Arab countries are looking for entertainment. And leisure in my spare time and work sometimes some of them, but not all
The goal is not to spy on such aforementioned projects, but the goal is statistical information about the users and thus about the society in which they are present because this gives indications of many economic, religious, behavioral, security criteria ... etc, and to emphasize that eyes remain open to everything in the world. In the end, political and ideological, of course, and part of it is economic.
And this is not limited to Apple only, but all system operators and all social media sites without exception .. because such topics are a prerequisite for granting licenses for such facilities.
ممتاز
Don't guys, what color download the program?
Very good
No answer !!!!
The topic is said to be double-edged
Thank you iPhone Islam
Would you like to solve the bluetooth problem from Apple ...
Its meanings of privacy are gone;
And the thief is disciplined and over the length of the prison ...
But the most important thing that misses my right is my privacy, especially that I am away from geleric and fear of its insecure vulnerabilities.
They are technologies that are not new, they are available for a long time and are available in all devices, but what Apple did here is to use these technologies in a new way. Who does not know that any official party can eavesdrop on any mobile device even if it is locked from here I want to remind you that the Internet is also It was present and used for several years before it became available to mankind, and we have to note that Apple here uses the available technologies to protect the owners of iPhone devices and increase the user's confidence for this device and also that Apple is the strength and luster of the device, it always maintains its marketing in various ways in an attempt And it is the most difficult, as we all know, and it is the preservation of the summit
By God, something strange, impulses and tension, but I do not say, but goooo, head and go with you to the other ... .. Greetings
The beginning of Apple's failure. If the jailbroken owner is not trusted, I expect millions of people to infiltrate their privacy
He was surprised by the happy people about the subject. I expect that there is a danger to Muslims, so that they can know their most accurate details
I hope he rejects this project, otherwise I am the first person to give up the iPhone
I hope your response was more objective and realistic !!!
Conspiracy theory
It still controls you
Apple's sales in America are enough
Yes, the issue is dangerous for Muslims because most of them use pirated (illegal) phones, and you may be able to disable them and deprive them of them !!!!!
First of all, I would like to thank Yvon Aslam and all his staff, and I congratulate them on the blessed month of Ramadan, may God restore it to the Islamic imams in Yemen and the blessings. Really hard. An amazing thing if they actually have a feature with these specifications. And he creates what you do not know. We can only thank the Lord of the worlds and thank you
Trust is the basis of the dealings between you and the company, and I believe that Apple is the best government on earth that applies and abides by the law
It protects and holds accountable, and I give it full authority. Do not be afraid. Do not be afraid, but the problem is if the thief does not use the Internet if there is no benefit from this invention, especially in our Arab world. The Internet is a means of entertainment and luxury and not a need and necessity, so you do not see its widespread and wide use as if you, Bouzid, did not invade
I mean, invent a ball and drink a loooooool water
Unless you turn on Apple Internet in the stolen device
And the ability to do so is the invention at the same time
It makes you think to what extent technology has been able to reveal our identities and privacy and control our devices
Believe my dear brother, Apple must have the same confidence that it places in its users
Today in particular, I replaced my XNUMXGS device from Apple Astor with a new one in less than XNUMX seconds. The employee decided to switch the device because the vibrator was not working
He did not ask me anything other than how can I serve you today
I started to fear the iPhone for myself.
I liked picture It was contained in a similar article in Mobily Arabic.
At the beginning, I am very, very grateful, O Aqaba, because I read the news more than once on famous foreign websites, but I did not understand it well, frankly ...
I expect that Apple increased it unacceptably, meaning the device to me and I am free with it, and I can download the jailbreak or throw the device in the garbage. What does Apple have to do with that?
I hope that Apple retracts its concept before losing the largest group of its customers
شكرا
Hi
To me, this is something silly now that China is fighting Google, the most popular search engine in the world. I pretended that he was a spy on her, and we got a company like Apple that spied on us, not yet with our own pictures.
Suppose the holder of the device, your sister, do you accept to photograph and publish her pictures.
Did we get to put our minds in the freezer and forget what the word spying means? One time he buys a laptop and immediately puts a sticker on the cam so that he does not take pictures of his family from intruders who are called hackers. And you rejoice to spy on you.
Apple did not turn away from you and your phones were stolen or not, and is it a guardian of your devices? All it has to do is seized and evaluated the device.
Beware of espionage and be like China, which has put in place a special engine for its people, which it thought Google was spying on.
Thank you Yvonne Islam for our continuous dedication to everything new.
But I do not, and I will not allow Apple to look at my privacy except what I allow it to do, meaning that Apple in this regard will look at every little one in your public and private life.
So, unfortunately, you will not succeed in implementing it from my humble point of view
Top hat tribute to this pioneering company.
Everyone has questions about this topic, but we do not want to rush until this invention is proven and applied. Certainly (Appl) has done studies on this invention and we hope to see it implemented and effective. Then this company will kick with its man every thief trying to steal these devices.
But I have a question about the program (Find my iPhone), is it real, accurate and effective as well?
Where can I find a full explanation for it?
The vision was not very clear
Is this technology software and thus will be included in an upcoming update, for example? Or hardware and will only be available on iPhone5?
Also, in case it is a software, will it be mandatory or optional?
In any case, the issue is very, very dangerous and of terrible proportions, so no one guarantees the wrong use of anyone, but from within Staff Apple or from hackers who have proven the fragility of the system in the last jailbreak ...
I think it is time to open source
Hey Android
Peace, mercy and blessings of God
An invention and the most wonderful, and I personally salute this wonderful interest and creativity, but this development has become a double-edged sword and requires taking care of it in addition to that it will enter terror in the hearts of thieves.
I personally thank you for reporting such interesting news and for keeping us updated and updated with Apple on these inventions.
Very nice, but if my phone is stolen, how will I inform the company and what data they will ask for me to search for the phone
Very fictional topic and its application is even more difficult
What if you use this service to spy on us… ??
Thanks, brothers
I see that it has jumped over the wall of the user’s personal interests, the most important of which is privacy. As you said, I do not like the method, the secret code I think is enough, and God knows
Big talk, but the jailbreakers must prepare their accounts ... even if they have legal powers / successful initiative and successful Apple policy and know how to use this invention in its favor.
As for the jailbreak, I feel that it is an unavoidable evil, and I prefer to steal my phone and replace it with another than to live with the bulk of the break
God and the greatest days of the (terrible) Nokia device, Arabic messages ,,
Bigger than the Napoleon revolution, now it became difficult to live without Brick shampoo.
The days will show you what you were ignorant of
The news comes to you from not provided
Before we lived without a mobile phone, can you go without it?
And you believe that they can return the mobile phone ... with the mind
That is, they can be found in America, Europe and Germany, but we have a little difficult. We are always excluded from development because everything we have is subject to a thousand transactions and a thousand licenses, and in the end it is disrupted and becomes forbidden.
Your words are fair ... if you make a jailbreak, you will get all that is in the Apple store and more, and all this without a single penny you pay
I think that Apple has started to enter the stage of vanity and exaggeration, which will eliminate it, even if tomorrow, it will be seen soon
With my great love and keenness for this device to survive the boom, which will lead to a significant decrease in the number of users.
If there is an agreement between me as the owner of a device and they have an agreement and it is confirmed that the device is not in my possession, and after my consent, you copy the data and then cancel it ,, no objection
But if she makes a sensing based on her suspicions, I refuse
Then how can I be sure that it will not use my data to harm me, or that it will not fall into anyone's hand to tamper with !!
I totally agree with Nouf.
But I did not like that this feature cannot be used without the net, as the thief may block any means of communication for the device with the net ..
And another thing ,,
I think if Steve Jobs offered this service in his own and distinctive way, most of us would say how we were able to live before this invention Hahaha P;
It is true that with the rapid development the issue of privacy has become a frightening topic, but I am not an important person and there is no point in spying on me << This is always my view :)
The truth is that this news is bad for Apple because it may cause the original users to fear revealing privacy and ease spying on them, so now I am writing a comment and I put my finger on the camera because I am not comfortable with this news
Genius idea, but I don't think it will be accurate to this degree
I swear a very cool idea I mean Hahaha !!!
A strange invention, but very dangerous and may cause problems if used in espionage, especially between spouses
Great idea and we hope to see it free soon
Haha
Gives you wellness p subject and received
I see that the service is good for them, but for us Arabs it is difficult once because it has privacy that will be with others, and I don’t think anyone will send everything on his mobile phone or he will let others know about his privacy
And sugar
Very cool, but I suggest that Apple does not perform all these security tasks except after submitting an official notification from the affected iPhone owner and his acceptance of these tasks and the resulting consequences
All that has been mentioned is a fantasy
How can (Jawwal) measure the heartbeat and tension of the thief and know his psychological state ??!
I expect the new update that the mobile will arrest the thief, report him to the police, and return to the original owner without any help.
I would expect it to measure pulse across the screen with my finger if he signed it
God knows
By God, you are sincere
Something fancy ... with imagination
And above all a science education
Believe God Almighty
Frankly, it is a powerful program and people are afraid of it to spy on some in the future
Thank you, and may God protect you
A good invention, but like what was mentioned in the article, this technology will expose the information if the device has a jailbreak function..and most people use the jailbreak..that means this technology will be ineffective but harmful
This is a wonderful and dangerous thing, but fear. How do they keep our privacy for us, and I want to know what is Jailbreak?
Almost all it is a program to decode the device ... it allows you to install non-original programs and non-Apple programs or iTunes which are Cydia programs
And you did not receive only a little knowledge
Everything in it we live is new, and what is new in it, and Yvonne Islam every day is new
Aaaaaaaa new from Apple
Privacy is not to be afraid of ... because these companies are afraid of prosecution and fines in the millions ... so do not be afraid and do not mind being careful
Very fabulous program
When can we obtain the program
Enjoyable, but its application and speed of determination of the location and the accompanying security measures in the event of the location of the thief of the device
The benefit of the service, especially in our highly developed Arab world, kills only from the womb of my Lord
Apple is always at the forefront in the field of applications. Please respond to some suspicions about this service, our experience with this company is very interesting
I suspect it will not be free
Ari, at the moment it is not possible
God knows
God bless you p article distinguished
Frankly, Apple made us crazy with its continuous innovations for the benefit of the user
As for the invention, this is in itself a miracle and it has been achieved, but how can we use it or can we use it in any country
Long talk, but how do you subscribe to this service, and if he follows me and gets a jailbreak? What is done, the device shuts down, no cell is stolen, and no one is spying on me if you sweeten the jailbreak or not
I never agree with this feature from Apple
They have to stay where it is now and there is no need to delve deeper into the characters
Phone was stolen and you have MobileMe and that's enough
It may cause problems while they are not oblivious to it, and this is definitely my personal opinion ... Thank you iPhone Islam for the continuous effort to provide correct and useful information to users
This is my first subscription here, and good luck
A great technique, but difficult to implement and frightening at the same time.
Very cool, but what after disabling the device, if it is found, will Apple be able to return it as it was?
A good invention, but the user must be careful to use it against, especially photography, Professor Tariq
Glory be to God ... .. teach man what he did not know.
See ??????? What will Apple come up with in the coming years ??????? Weird !!!!
I am a supporter of this topic, but how is it implemented and how to subscribe because I’m tired of being stolen from me more than an iPhone, and every time I have my photos, numbers and e-mail lists surrounded, and now I’m going to the nearest agent to inquire ... ..
The service is great in every sense of the word, but the most important question is what is the user’s status if the company proves that he is a jailbreaker
Is it possible that he is legally required by Apple?
This invention has its positive aspects, but I personally think that its disadvantages may not be spared by any of the jailbreakers.
(((Frankly, the topic is intimidating))))
Jailbreak is legal
Very bad service, a clear and scandalous breach of privacy.
I agree with you
God is a strange technology that comes to mind
And God is excellent news. Let people with weak souls stop stealing
In the name of God, and that God only conceal us
They do not care about you .. they only have Al-Hatsi .. they are left without knowing the blood type of the thief ..
Peace be upon you ,
Apple is a company out of competition ...
I am afraid that one of the opponents of the iPhone will make a comparison between this mythical device and the old stubborn mobile and say that the stubborn is superior to the iPhone by knowing the number of letters of the short message, while the iPhone lacks this feature…!
Apple is a company that cares about what competitors don't think of.
Thank you for this article
Apple's serious frankness and a topic that deserves the proposal and includes a breach of privacy. Thank you Yvonne Islam for the interesting and useful topic.
I expect that this breakthrough will benefit the developed European countries and America, or here I do not expect it to succeed.
If I am a month ago, I stole my iPhone, and while I am sad, I think Apple is showing this organization
Too hard to conquer
In general, God willing, we will not steal our iPhones so that we will not benefit from this system
Thaanix (iPhone Islam)
Apple has the right to do so, but must change its software policy. It must accept the opinions of users and explain not to accept any suggestion in case of rejection.
I am in favor of intellectual protection, but with open areas. For example, RealPlayer
If what is mentioned is correct ... Very creative
Yes, I think that this company always brings strange new things.
It is not strange for a company with experience and old experience ...
In general, I think that this program will have great resonance and success.
"Thank you iPhone Islam"
Really a very powerful invention
(And you have received only a little knowledge)
Determine the thief's heartbeat
..
These are very strong
رائع
thank you
As long as the jailbreak is legal, there is no excuse for Apple to consider the user untrusted, especially since it is the first, main and only reason for users to do the jailbreak.
Hi
My brother, I am the first time I participate
But do you expect that, for example, I bought a device and took my photos, and on the second day I sold it to anyone, will the system be applied to it ???!
May God grant you success in this magnificent edifice
Accept my traffic
God is a sweet idea and he is admired by everyone.
This is the beginning of the end. No Apple if they focus on developing the shape, developing the operating system, making an open source, and nullifying the monopoly. Yes the monopoly. When you take a device with the contract for two years and the contract expires.
Glory be to Allah
And he taught a person what he did not know
Believe God Almighty
And if someone has a used iPhone device, the seller can spy on the buyer ????
And if someone stole the device and Sawa formate, delete the program ??
The sweetest and most wonderful two questions I heard in the comments
I like it and I think the answer to the second question is that they walk on the Siris number and the Internet to spy on
Really effective technique
But it is dangerous
That is, if Apple could shoot with my device from a distance, I would be concerned about my privacy
Or suppose this technology becomes accessible to those who misuse it, it is a disaster
This is my opinion, knowing that I am not an expert in such a technique, and is it possible to spread it to those who do not use it well
Thank you iPhone Islam for conveying such news in order to be in direct contact with what is going on around us
Brother always look to the bright side
And don't think about the dark side
If we stay on your words, we will not develop ourselves
God bless you, my dear brother
And thank you for your response, may God bless you
I am completely confident that I am an evolutionist
And my previous response was not to accept this unique technology
But we must not lose sight of the negatives and try to address them
And I think that a big company, the same Apple, is not wasting all this reputation and prestige and spying on its customers
But the fear is that this technique has fallen into the hands of those who are not in good use of it
I would love to respond to those who are surprised by the word ((espionage))
And I do not mean by her to conspire against me to take the seat of judgment from me :)
Rather, the fear of revealing pictures of our people
I hope the picture is clear now
Thanks again
A very very excellent idea
Hi
By God, this is a very natural and beautiful invention, especially when taking pictures. This is a wonderful idea. Apple does not give you something new every once in a while. Beautiful, Apple
A very beautiful technology that increases the beauty and magnificence of the iPhone
This really distinguishes Apple, as it is always rushing to the top
I have a question
How this invention was used
This is just a patent, and it may not be implemented by Apple, just an idea that Apple registered in its name
Something beautiful, but I expect something difficult
Wonderful and terrible invention, but praise be to God the majority will not need this invention because it is ?????? Thank you
New and distinctive idea
But how to subscribe to it, How are you ??
This is just a patent, but it may soon become a reality.
For myself, I strongly encourage such a technique
This is a Tamaamah privacy, so let him bear its consequences before subscribing to it
It remains and remains a double-edged sword
Apple Apple Apple; How amazing you are, Apple
Very difficult and frightening, especially for us women. Honestly, I began to doubt that the iPhone takes my picture afterwards. These are inventions or proposals that I expect that they are old and planned for a long time because of the material only.
Apple is impossible to think about and ruin its reputation
Suck up money !!!!
Believe me, they deserve every penny
Free software is abundant, and the rest is cheap and affordable
And all the basic programs are free
Where are the losses !!!
But people pay for excellence.
Wow, amazing thing
Frankly, this technique is very nice
But is there a technology like this for the iPod?
I think this technique will not work when you disconnect the internet from the device
Is this true ?
نعم
Here is the problem
The thief knows that the internet is the connection to these things, so he turns them off, so here I say stop
From my point of view it is good and not good at the same time
Really good exit for thieves :)
Mkkurien p coverage
Very awesome creativity
Of course, I am totally opposed to such a technology that it permits itself to violate your privacy without even asking you to ask me. Tell me what will happen if the device is photographed while you are in your bedroom?, Or if this device is for a veiled woman? And he must make sure of your location, this is nothing but a spy device, and then the iPhone is just a mobile that has gone, and there is no way it is a mobile, so why all this computing was the first in the car companies to implement that? Is it so that the benefit is felt when your car is being stolen? By God Almighty, this is something that burns blood, and we don’t want to smell someone because we are in Ramadan.
Allow me to show you completely regarding your word that the iPhone
IPhone exceeds the limits, it is a mobile to call only
I follow my work daily through the iPhone
Organize my time via iPhone
I put my light books on the iPhone
Browse my emails via iphone
The complete master's thesis is in the iPhone
I dispensed with the two video cameras after the iPhone XNUMX because it has the HD feature
My entertainment on the iPhone
Browse newspapers daily from the iPhone
In the end, the call is from the iPhone
Allow me to tell you that the iPhone crosses the limits of a mobile phone
I know perfectly well that he has crossed the mobile phone barrier and with great steps in the world of technology, but I am talking about the idea that it is just an entertainment thing. If the world goes away, it will not stop. I mean, imagine that you woke up in the morning. It contains your emails, your work, and any insignificant mobile that you can turn on by an alarm. I mean, this does not completely detract from the iPhone. Rather, I mean that it is a secondary thing. You are not alone with him, but it remains an annoying thing
Unfortunately, your words indicate that your blood was burned
And as if you were living in a society free of espionage
But I guarantee you that the privacy of iPhone users at Apple is capital and one of its most important priorities
The leakage of anything from the company is considered a great insult to it and its employees, and it will not be accepted
I will ask you a question: I am when I say that I am afraid of the device portraying its owner in a situation that is not pleasant, by saying that because of the people who are not working in Apple, they are the ones who don’t feel it. In short, Apple would be better if this was done by asking the customer, where he chooses the type of data that he agrees to verify
The confidentiality of user data is privacy that no one has the right to spy on ... As for the jailbreak users, considering them as untrustworthy is something that no one can bear ..
My opinion is that not every patent is actually usable
Thank.
good idea
I congratulate Apple in its rapid development
And the creator
It has a great risk of breaking into privacy, and from another view it is good because of its safety.
By God, I think that what they want will do it always. We use what is offered to us and whoever criticizes finds a hundred ignorant people to silence him. I live Yvon Islam on their activities and I hope that every Arab like you thinks about making something that does not take what is offered to him and waits for the West to give him more. You are the ones who introduced the Arabic language. To the iPhone, from which I am responding to you now, thank you and I wish you continued success. And the Imam is always with God
Wonderful program, but has the program been tested?
Can it be used for espionage?
We sleep in Apple ,.
My opinion is that this company is one of the most pioneering companies in the world and deserves a lot. As for the jailbreak, I am not with it in its illegality except after it provides us with everything we find in it from flash (mattress) and SP will be divided, themes and many programs that make it easier for us to use this device and increase Of its splendor
As for taking pictures, they will be useless, because the one who will steal the iPhone from now on has become aware that he must drunk his cameras.
All in all, believe me with this new news and security update, the stealing of the iPhone has become something that does not have to do with this device, which will be photographed for XNUMX hours, and the thief will not let the thief rest until after he has stolen it.
My message to everyone who wants to steal iPhone, if you steal tobacco you steal, I steal it just to break it, you will not enjoy it :) And this is what Apple wants, it's really cool
Hahahahahahahahaha
A great idea for Nokia owners
Steal it for cracking
Very beautiful and I wish they imprison the thief too
:)
In the next update, we are waiting for him to contact the police, to arrest the thief, and to return the iPhone without our knowledge. Oh and he will be attending the café in the morning
Honestly, a technique in the summit of Roooooooooooooah
Frankly, I love to protect my device from intruders and at the same time protect from theft
This is a great idea about heartbeat, but even if they can achieve it, how will they be able to differentiate between pulse and for jailbreak?
And I wish they could implement this technology that they make it optional
Thank you for the article :)
Thank you for the topic, even if it came a few days late and we read it how many days ago, but this is the best explanation of this patent
Thank you, Yvonne Islam and forward, and we await the latest company news
Frankly, it is a very wonderful technology and it will bring many users to other smart devices because of the comfort and reassurance of the user in the event of theft or loss of his device.
But what about the issue of jailbreakers? !!
Will this technology include them or not? !!
The coming days will answer many questions that are on everyone's mind !!!
Right
Apple WPS
The only problem is bluetooth
I hope that no one of these techniques is used to spy on or eavesdrop on others
And God will show them what they invented if they jerked against someone who uses jailbreak and who is personally convinced of its legality.
In general, this I consider it a security vulnerability rather than a pleasant thing, because our information and all our privacy, according to the article: are transferred to a remote server !!!! Who said that we want that or that we trust blindly in Apple employees and Apple's security relations with some governments !!!
Indeed, as the author of the article said, Apple has a lot to announce and clarify if it launched such technology. The privacy of the owner of the Apple device is his only, and the company has no right in any way to copy it or keep it in (a faraway place) !!.
Thank you for your wonderful news, and you rewarded you well.
Really I agree with you, may God only conceal it
Oooooooo my fear remains a shameless espionage method, no seriously, I am not assured
true, you are right
The world, which is ours, we love and enjoys spying, accessing any confidential information and inspecting privacy.
Why?
Because there is no benevolence to us
The problem for every invention and its positives must be to think about the hidden negatives and their damages, meaning that it is correct to think from the other side and not from one side.
Perhaps I agree with you that it may be an espionage tool, but to whom and for whom?
Some governments have influence over some individuals who are targeted for their positions or the like.
As for us people, no one knows about us :)
I was mistreated between me and you, let them spy with their hands and feet.
God is great, Prime Minister, when I fear that they are spying on me and like me a lot, but some have espionage obsession.
Of course I mean a specific person with this talk
Honestly, if this invention is applied, it will overwhelm the markets and embarrass the rest of the mobile device companies with this idea that no one has ever thought of.
Nice idea, but I think its implementation is very difficult
I agree with you
Even if it was implemented, I think that the percentage of benefit from it will be low
And what if we know that the thief is nervous or not may have a slight benefit, but from my point of view only that the effort expended is greater than the output
And thank you iPhone Islam
In the world of technology there is nothing difficult ,,,
But the issue is bigger than that ,,, to what I understood that Apple can activate the device by photographing, recording and locating the location, and this technology if it falls into the wrong hands may be a disaster ,,,
Is it possible in the future to fly to cover the camera for the iPhone as we do with a laptop ^ _ ^?
I hope for the correction if my understanding was wrong
In the name of God the Merciful
The ideas included in the patent can be exploited in more than one way and in an excellent way, for example knowing the location of the iPhone and determining the heartbeat of the iPhone.
These two features and others can be useful to us .. I think the ideas are serious, but they must be reformulated and used in different ways
And it ends before my iPhone is stolen, God suffices for whoever stole it
May God compensate you
Hey guys ... if Halsey is really worth it, then this is a wonderful achievement that should be added to her accomplishments ... And if the site is bad, it raises the story of the jailbreak, its legitimacy, and the loss of the user of Apple services while the device was using a jailbreak ...
Frankly, I do not believe in generation break ... I tried for a while, and after that I went back to the basic system .. Praise be to God, that my Lord honored me with my device that is open to all networks, but as the generation of blessings has positives there are also negatives which in my personal opinion lose the iPhone's pleasure ...
There is no doubt that there are many great additions to jailbreak, but remember ... the device in your hand is an "iPhone!"
I was obsessed with Nokia devices ... and its system and a lot of features in its system, which until now the iPhone lacks "except through jailbreak" such as the message delivery report, international number recognition, bluetooth ... etc ..
But I forgot all these positives, and my sister ignored their importance as soon as the iPhone was in my hands ...
What do I need for bluetooth, for example, when I have a device that can, through the software store, give me any application or any music file I want?
What do I need for the Bluetooth with a sophisticated browser in my hand that can give me any image or file I am looking for?
Isn't that true? ...
Sorry for the prolongation, but the developers in Apple were very tormented until they reached this wonderful preparation “or other Apple products” and we must at least respect their efforts and even send notes to them so that the deficiency develops in their systems ...
Thank you icon Islam ... :)
Well done
What I need and everything is in my hand
I tried the gel break and I didn't like the 3gs
Now I have iPhone XNUMX and I don't think at all about the bulk break
Thank you for this wonderful comment
Really, this is what we need, and it is sending an opinion to the designer to develop ideas and avoid mistakes
Accept my greetings